Identify the System Constraint
Identify, add detail, actionable? Identify, add detail, actionable?...
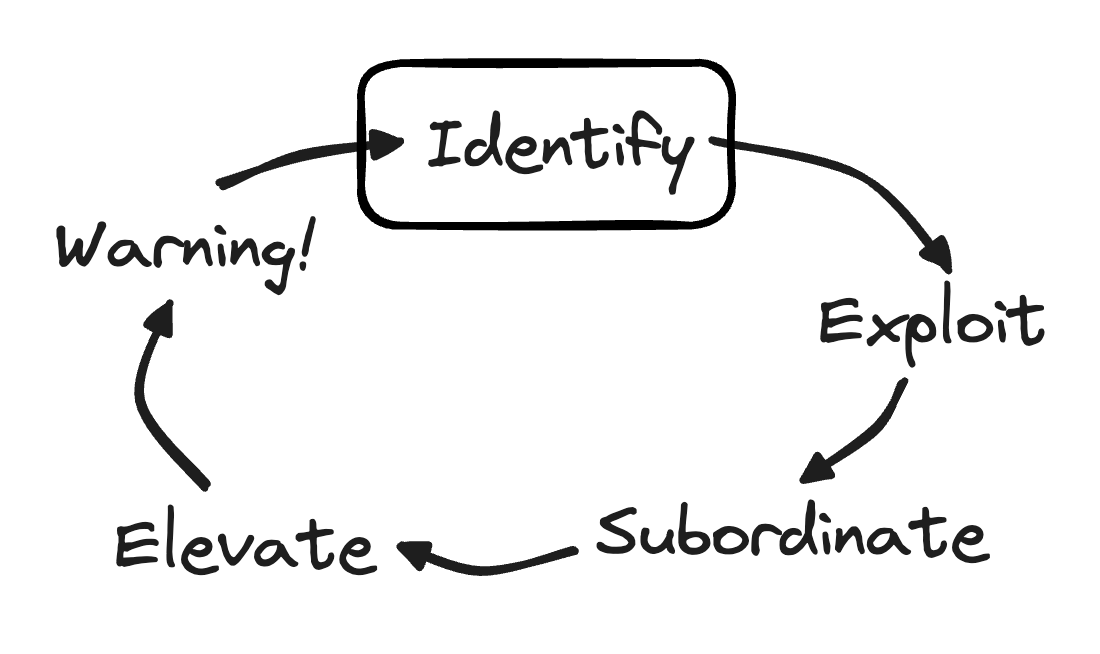
Starting with the simplest Value Chain of the system you selected, this first step is to identify the system Constraint. Our goal at the end of this step is to end up with a clear and actionable Constraint identified.
To accomplish this, you will repeat a process of identifying the Constraint on the Value Chain, then, as needed, you will add minimal detail in the Value Chain. You will continue until a clear and actionable Constraint is identified.
As an additional benefit of identifying a clear and actionable Constraint, you will end up with a Value Chain with the relevant amount of detail to provide context for the Constraint you are addressing.
We will use the Tea Shop example throughout to demonstrate each step and possible outcomes.
You may use the Tea Shop example as a reference, but you should apply each step in this guide to your specific system instead.
Need help? Schedule a free 30min session
If at any point you feel like the guide is unclear or otherwise unable to help you, schedule a 30 minute session to get help. Your experience and feedback will help improve this guide for you and others.
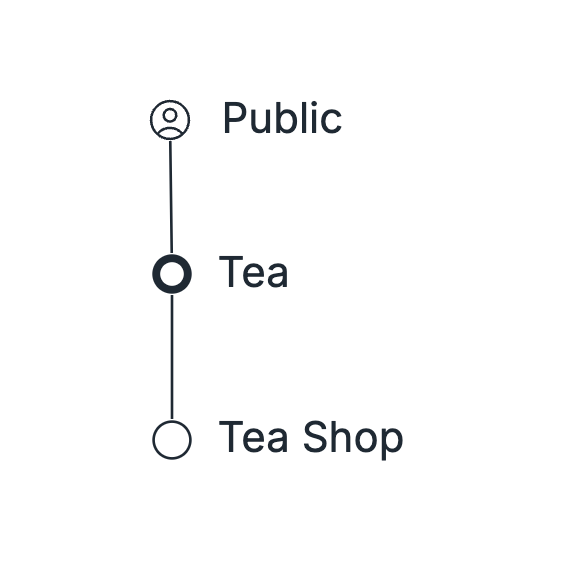
At the start, with the initial Value Chain, we have only three options of where the Constraint could be: User, User Need, or Component.
First step is to identify which of the three options has the Constraint.

If the Constraint is with the User
If the Constraint is with the User, consider for a moment what that implies. It implies that we have a User Need and a Component that fulfills that need. In the Tea Shop example, if the Constraint is the Public, that means we have a Tea Shop that can readily fulfill the current need for Tea without a problem.
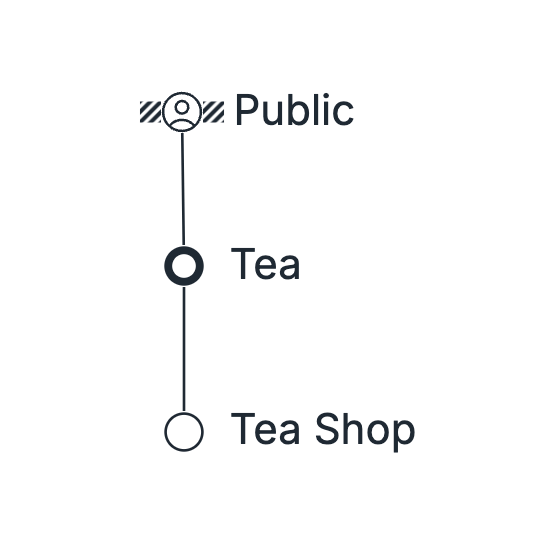
In your system, if this is the case, mark the constraint with the User. Go to User Constraint lesson.
If the Constraint is with the User Need
If the Constraint is with the User Need, it implies that we have the Public readily available and that the Tea Shop is ready to fulfill any need for Tea that arises. However, it also means that the Public doesn't seem to actually want Tea, or at least not want enough of it.
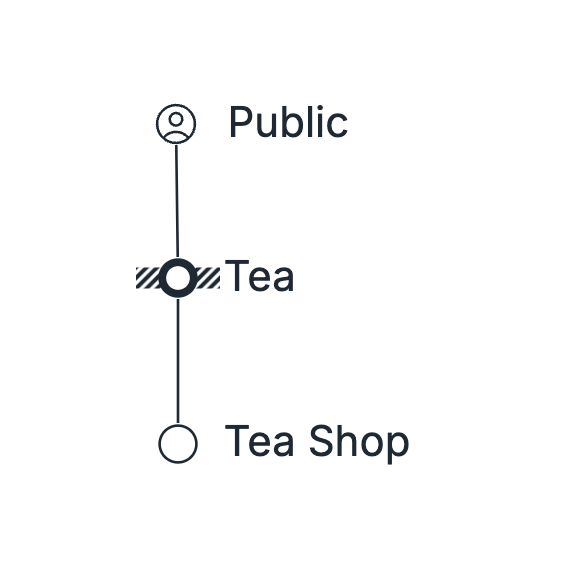
In your system, if this is the case, mark the constraint with the User Need. Go to User Need Constraint lesson.
If the Constraint is with the Component
If the Constraint is with the Component, it implies that we have the Public readily available, they want Tea, but the Tea Shop is unable to fulfill the need for Tea from the Public.
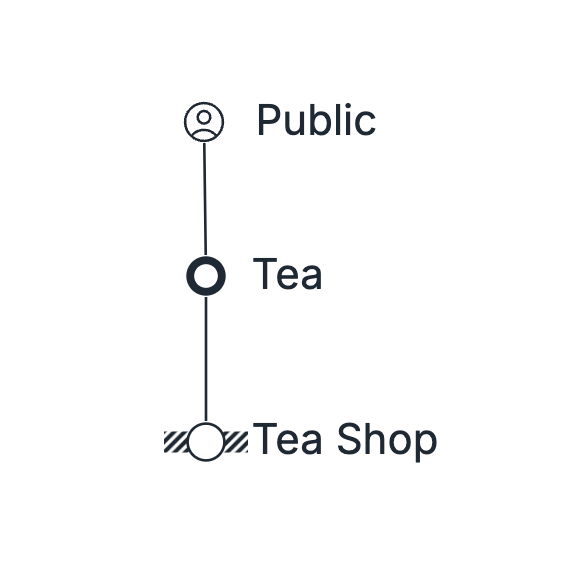
In your system, if this is the case, mark the constraint with the Component. Go to Component Constraint lesson.
Go back
If a Constraint Has Been Broken, Go Back to Step 1
Explore the critical step of avoiding inertia in the process of managing a system's constraints. Learn the importance of re-evaluating policies and procedures after elevating a constraint to prevent outdated practices from becoming new bottlenecks. Understand the application of Wardley Maps in identifying and addressing obsolete policies to ensure continued system efficiency.
Up next
Decide How to Exploit the System's Constraint
Learn how to maximize the efficiency of your system's constraints and ensure no resources are wasted. Discover practical strategies to exploit your constraints and increase the overall value delivered by your system.
