Subordinate Everything Else to the Above Decision
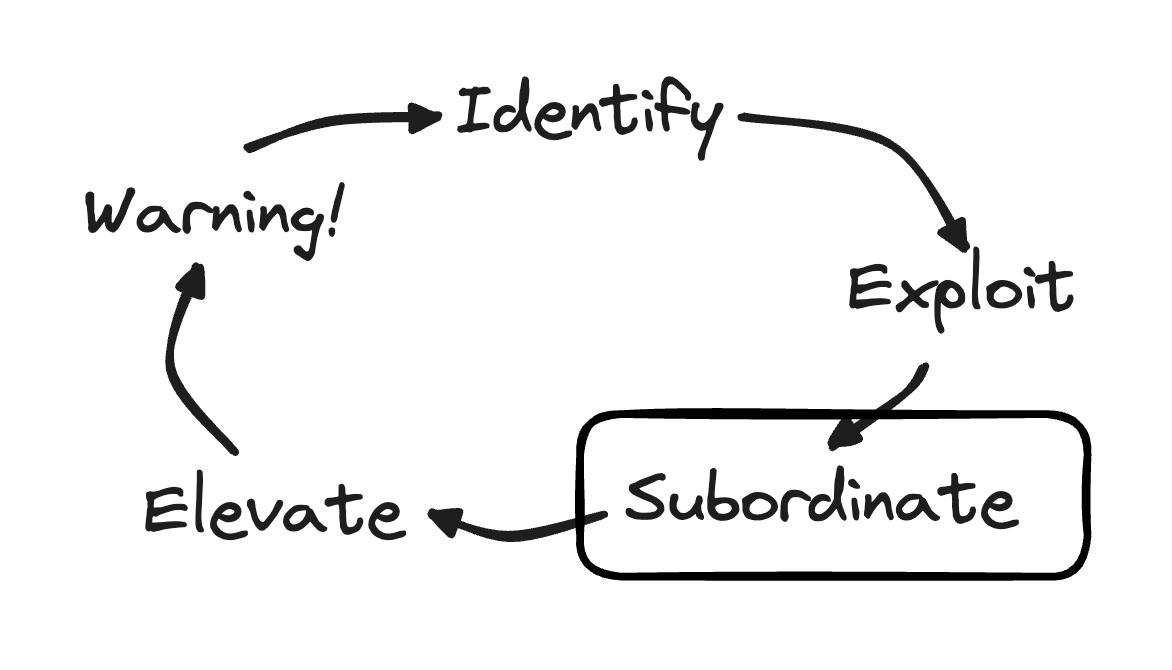
Constraint inputs and outputs
At this point you should have a Value Chain with a Constraint and a decision on how to Exploit the Constraint. Now, we will Subordinate all the non-Constraints to the decision.
First, we will need to identify all the relevant non-Constraints. What makes a non-Constraint relevant? At a high level, a non-Constraint is relevant if it provides input to the Constraint or accepts output from the Constraint.
To help you identify the relevant non-Constraints, you will repeat a process of identifying Constraint inputs and outputs on the Value Chain, then, as needed, you will add minimal detail in the Value Chain. You will continue until all relevant non-Constraints are identified.
This step will once again grow the level of relevant detail of your Value Chain. This time, the focus of the detail will be on Constraint inputs and outputs instead of the Constraint itself. While identifying the relevant non-Constraints, you will be Subordinating them to the decision on how to Exploit the Constraint. If we want to maximally Exploit the Constraint, we need to ensure that all relevant inputs and outputs are available and the Constraint is never disrupted.
Need help? Schedule a free 30min session
If at any point you feel like the guide is unclear or otherwise unable to help you, schedule a 30 minute session to get help. Your experience and feedback will help improve this guide for you and others.
Subordinate steps
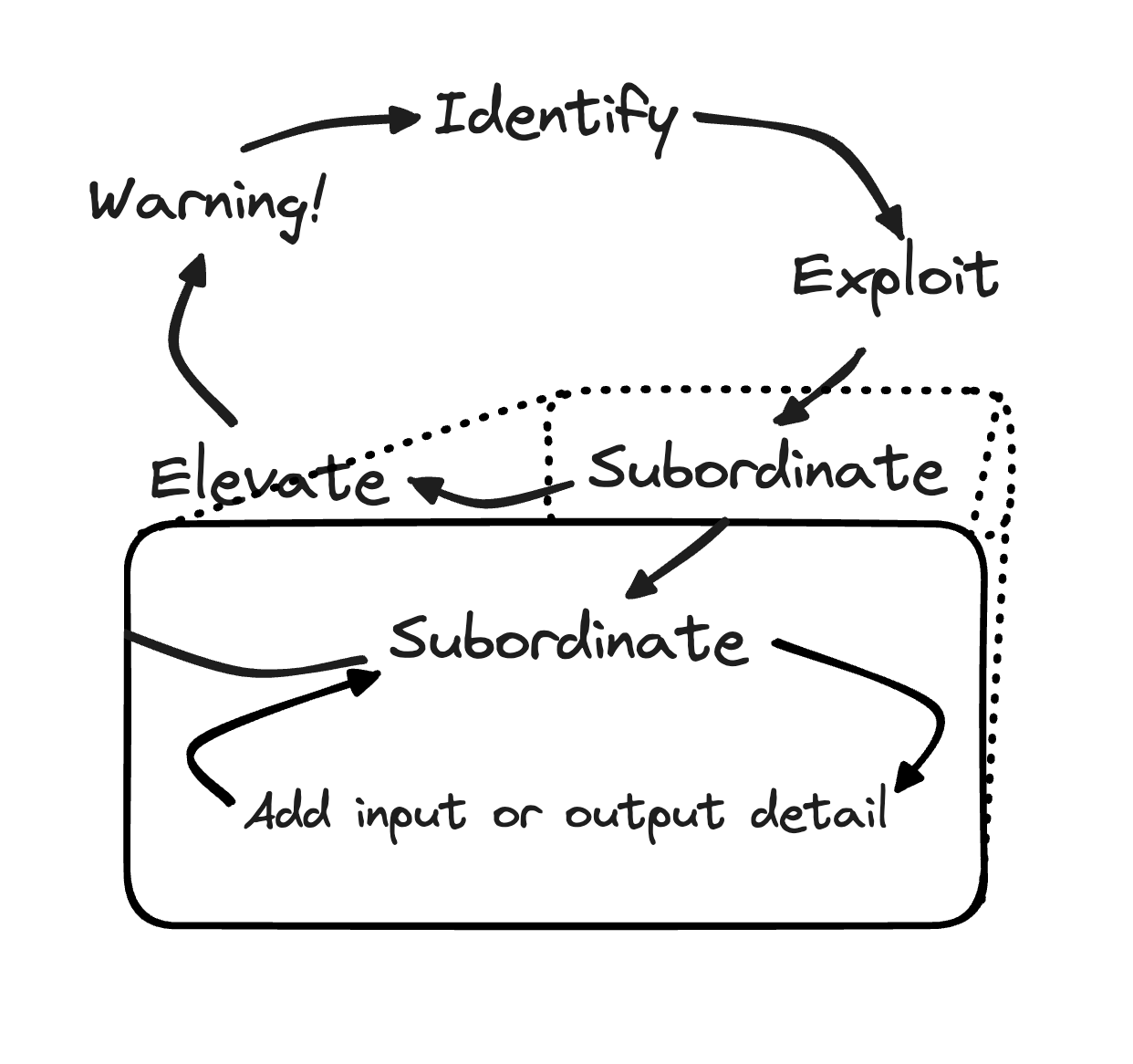
- For the Constraint or one of its inputs or outputs, add a single input or an output.
- Select actions to take to Subordinate the input or output to the Constraint.
Repeat these two steps until you feel that you Subordinated all that you can to the Constraint.
You should be taking action
It is important to note here that these are action steps, in that you should now be taking actions within your system, affecting change and observing for improvement in utilization of the Constraint. These steps may take some time and you may have work to do. Ideally, you want to end up in a place where no Constraint capacity is wasted.
Let's illustrate some of the different things that can happen during this step using our Tea Shop example.
If the Constraint is with the User
We will continue with the following Tea Shop example.
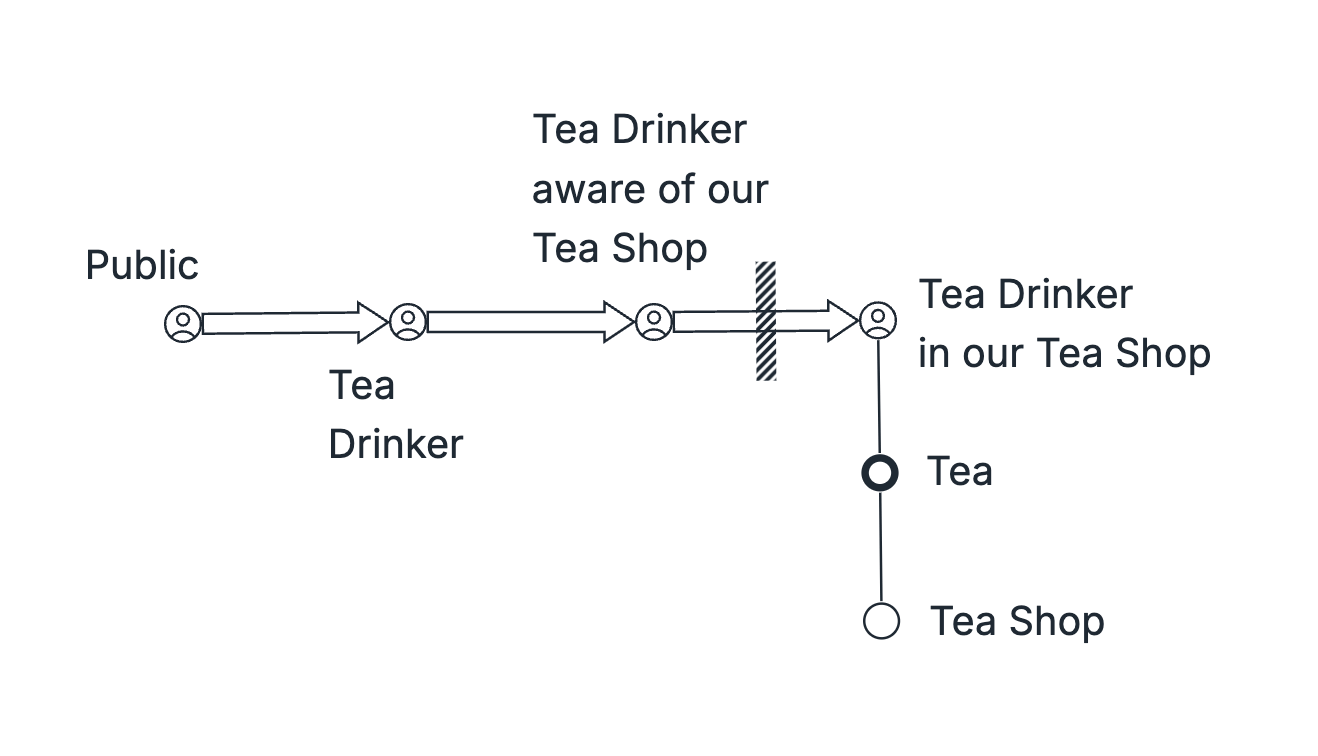
Go to Subordinate to User Constraint lesson.
If the Constraint is with the User Need
We will continue with the following Tea Shop example.
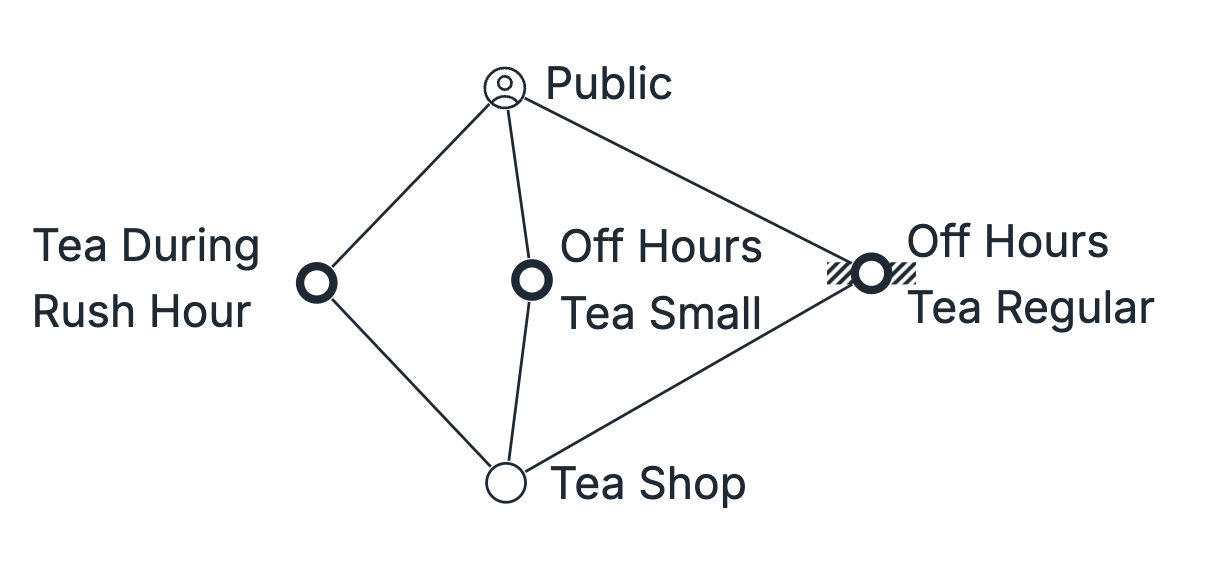
Go to Subordinate to User Need Constraint lesson.
If the Constraint is with the Component
We will continue with the following Tea Shop example.
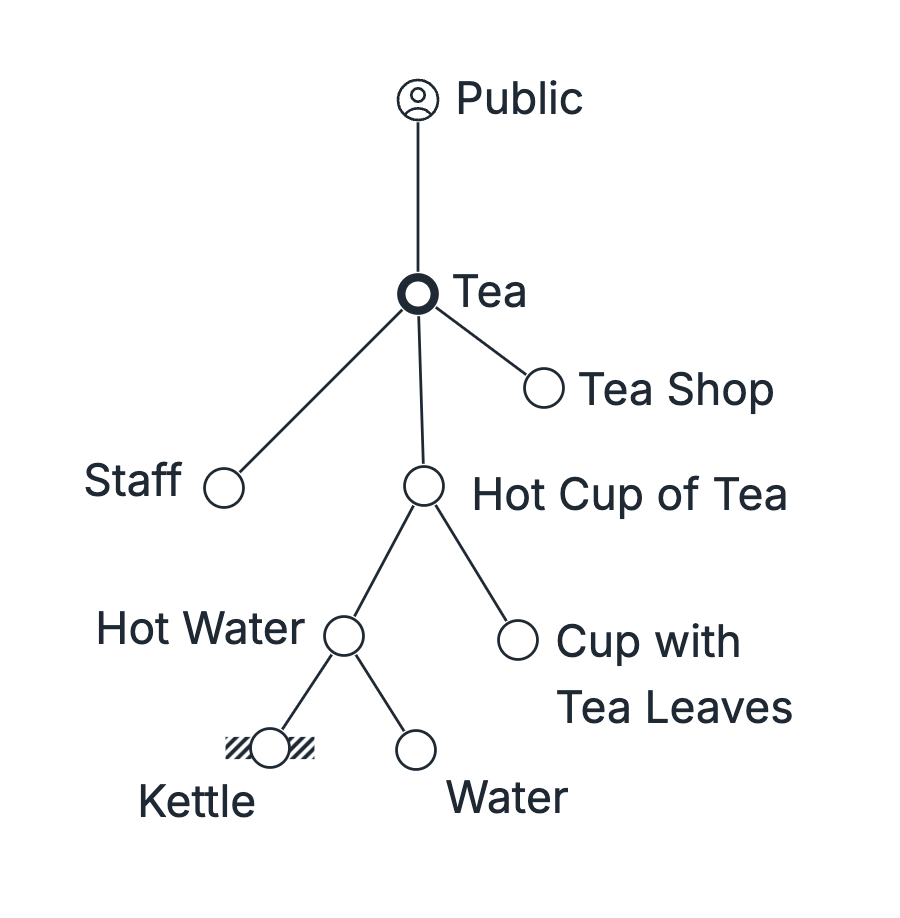
Go to Subordinate to Component Constraint lesson.
Up next
Once you, with your system, reach the point where you are maximally Exploiting the Constraint, you are ready to proceed to Elevate the System's Constraint lesson.
Go back
Decide How to Exploit the System's Constraint
Learn how to maximize the efficiency of your system's constraints and ensure no resources are wasted. Discover practical strategies to exploit your constraints and increase the overall value delivered by your system.
Up next
Elevate the System's Constraint
Explore the process of elevating the system's constraint by stepping out of the process flow and considering evolutionary stages. Learn how to identify, exploit, and elevate constraints within your system.
